The Maturity Trap: The False Confidence of Maturity Models
We’re flooded with best practices, compliance frameworks and an ever-growing list of security tools promising comprehensive protection. A simple maturity level, tier or green dashboard is powerful. Everything looks and sounds good, because you’re getting top ratings. However, cybersecurity is a complex and ever-changing field.
The promise of clarity looks good for board reporting, vendor management and cyber insurance. “Tier 1” feels like a shield, your cybersecurity defences are verifiably strong.
This is a dangerous illusion, built on a fundamental disconnection between external appearance and internal reality. Many common security practices provide more comfort than actual protection. This false sense of security is a critical vulnerability in itself.
Cybersecurity maturity ratings typically operate from the “Outside-In” perspective, fundamentally blind to the “Inside-Out” context where security usually succeeds or fails. Critical business-ending risks often lurk in these shadows: human behaviour, internal application logic, shadow IT, etc. Attackers thrive in in this gap between perceived safety and operational reality.
This article will explore the counter-intuitive truths that lie beyond security maturity scores, and why these often take the focus away from critical areas in need of attention.
A perfect rating can be a prelude to a catastrophic breach, and has been in a number of high-profile breaches. The real measure of security is not found in a score, but in operational resilience. Understanding this truth is the first step towards building a truly resilient defence.
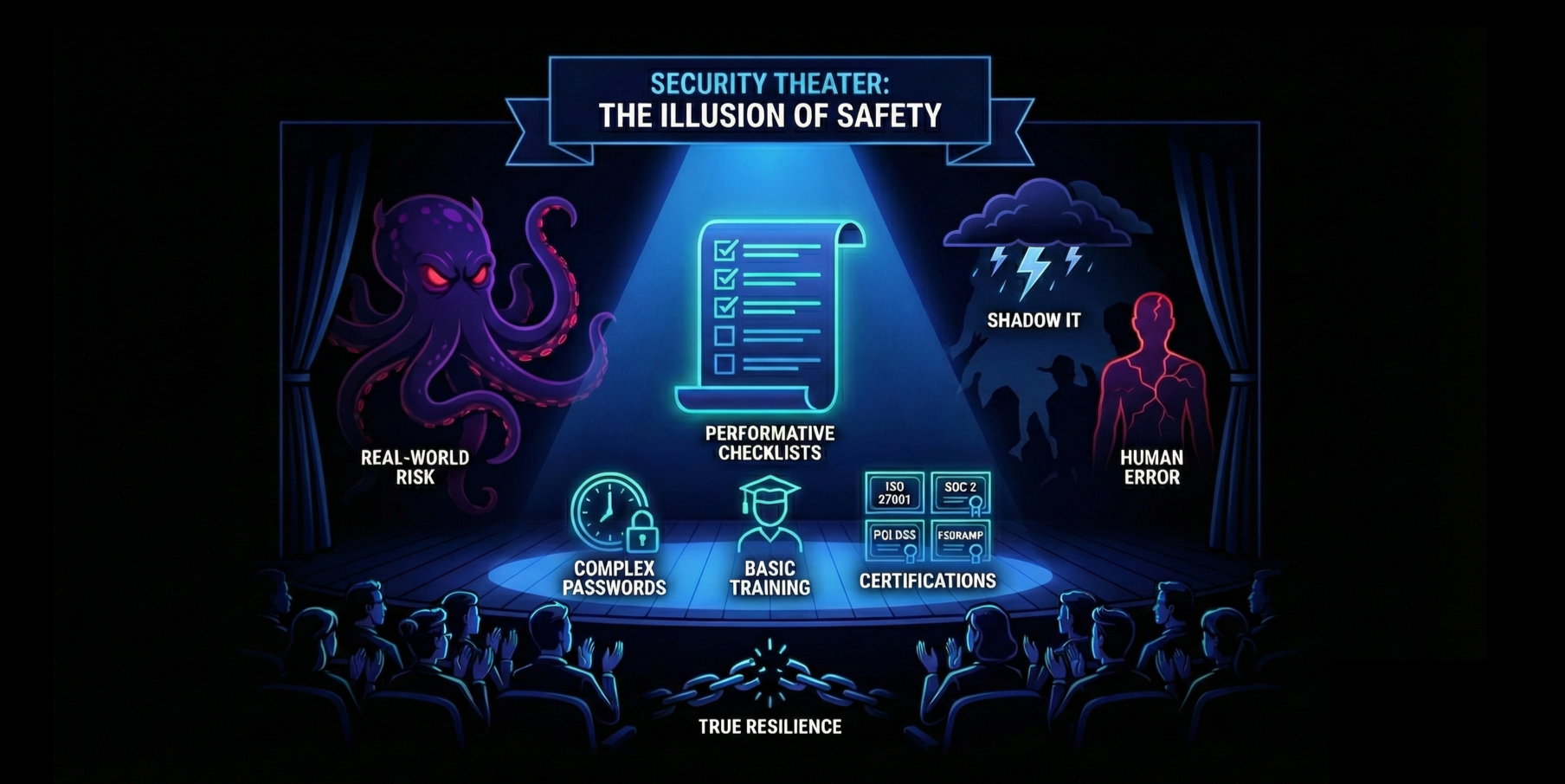
Your Security Checklist Might be a “Security Theater”
“Security Theater” (coined by Bruce Schneir - Beyond Security Theater) is used to describe actions that make people feel safer, without actually improving their security.
In the cybersecurity world, this manifests as a focus on “checkbox compliance”; fulfilling a list of security requirements regardless of their real-world effectiveness. The goal becomes satisfying audit requirements rather than mitigating tangible risk.
Prime examples of these are prevalent in many organisations:
Overly complex password policies requiring 90-day rotations, despite NIST now recommending against them (NIST Special Publication 800-63: Digital Identity Guidelines - Q-B05).
Security Awareness Training that is well-intentioned (and effective in some organisations). Data shows that in 2025, 60% of data breaches continued to involve the human element. (Verizon - 2025 Data Breach Investigations Report)
Compliance (or roadmap to compliance) with security frameworks. Organisations such as Solarwinds (ISO 27001 certified and SOC 2 Type II attested), Equifax (ISO 27001 certified), Target (PCI DSS compliant) and Okta (ISO 27001 certified, FEDRAMP compliant and SOC 2 Type II attested) were all breached, proving that compliance tasks can fail between audits.
These performative measures offer the appearance of diligence but fail to address core risks.
The real danger of “Security Theater” is that it diverts finite resources (time, budget and attention) that should be focused on the most significant threats. While teams are busy managing password rotations and fixing vulnerabilities that aren’t contextually risky, critical risks like Shadow IT (unapproved technology) and thorough third-party risk management are often unaddressed, leaving the organisation’s most valuable data exposed.
We need to shift from activity-based (signature-based) security to risk-based (behaviour-based) security. This focus on performative checklists not only wastes resources but also creates a critical blind spot for how attackers actually operate today: typically without malware.
Security Ratings Tell an Incomplete Story
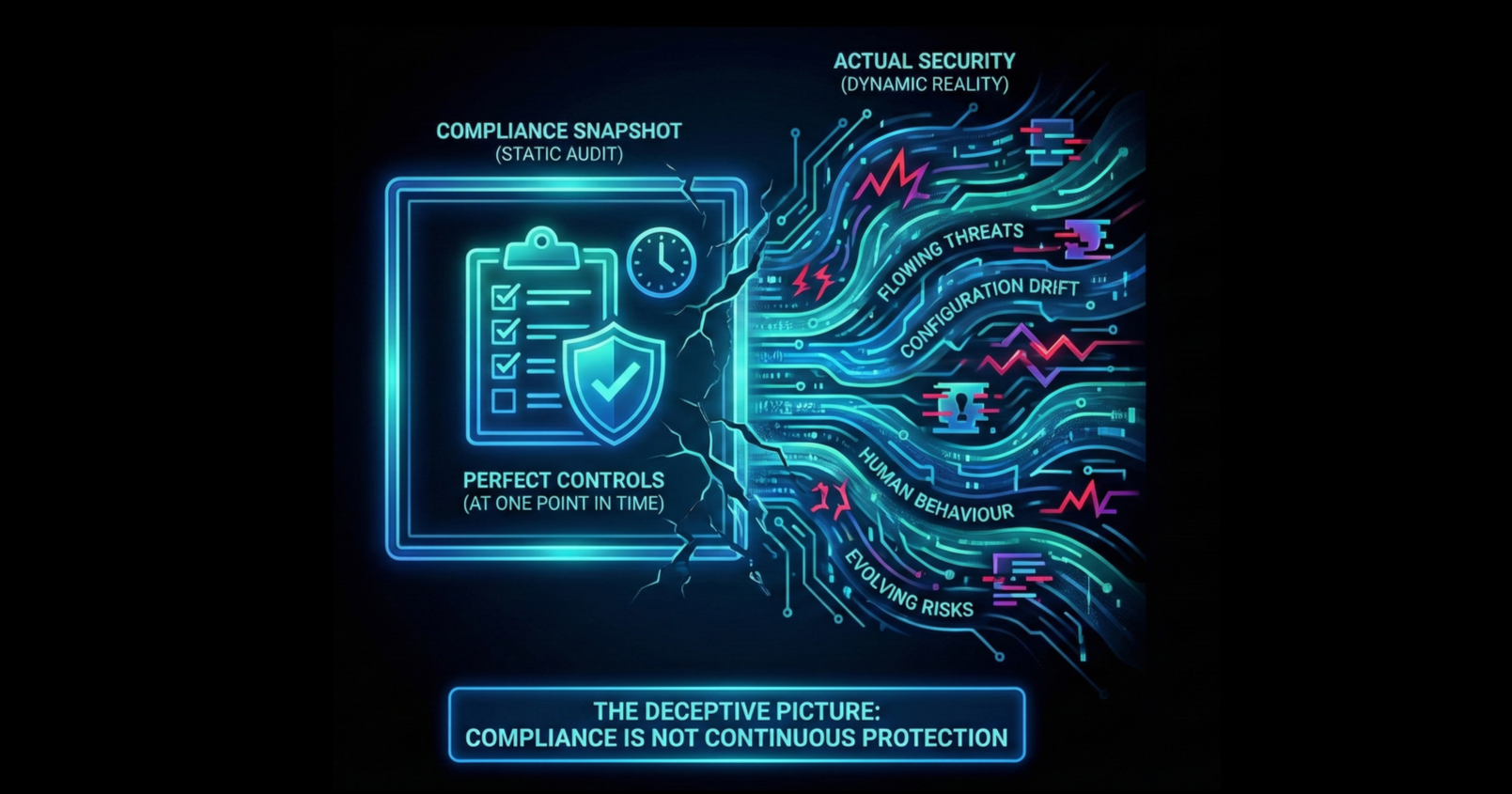
Compliance and security ratings often provide a deceptive picture of an organisation’s safety because they fundamentally measure adherence to a specific set of rules at a single point in time, whereas actual security requires dynamic, continuous protection against evolving threats.
While regulatory frameworks establish necessary baselines, they cannot account for the fluidity of modern cyber risks, human behaviour or the rapid changes in an organisation’s digital environment.
One of the most significant limitations of compliance ratings is that they are typically ‘snapshots’ taken during an audit. An organisation may demonstrate perfect adherence to controls on the day of the audit, yet suffer from ‘configuration drift’ shortly after, where settings gradually misalign with policies due to updates or manual changes. Consequently, a ‘snapshot’ doesn’t guarantee the control remains secure the next day.
Attackers don’t adhere to audit schedules, threats are continuous and attackers can exploit vulnerabilities that arise between assessment cycles.
For instance, Verizon’s forensics team noted that while organisations strive for PCI DSS compliance, they have never found an organisation that was fully compliant at the actual time of a breach (Verizon - 2015 PCI COMPLIANCE REPORT).
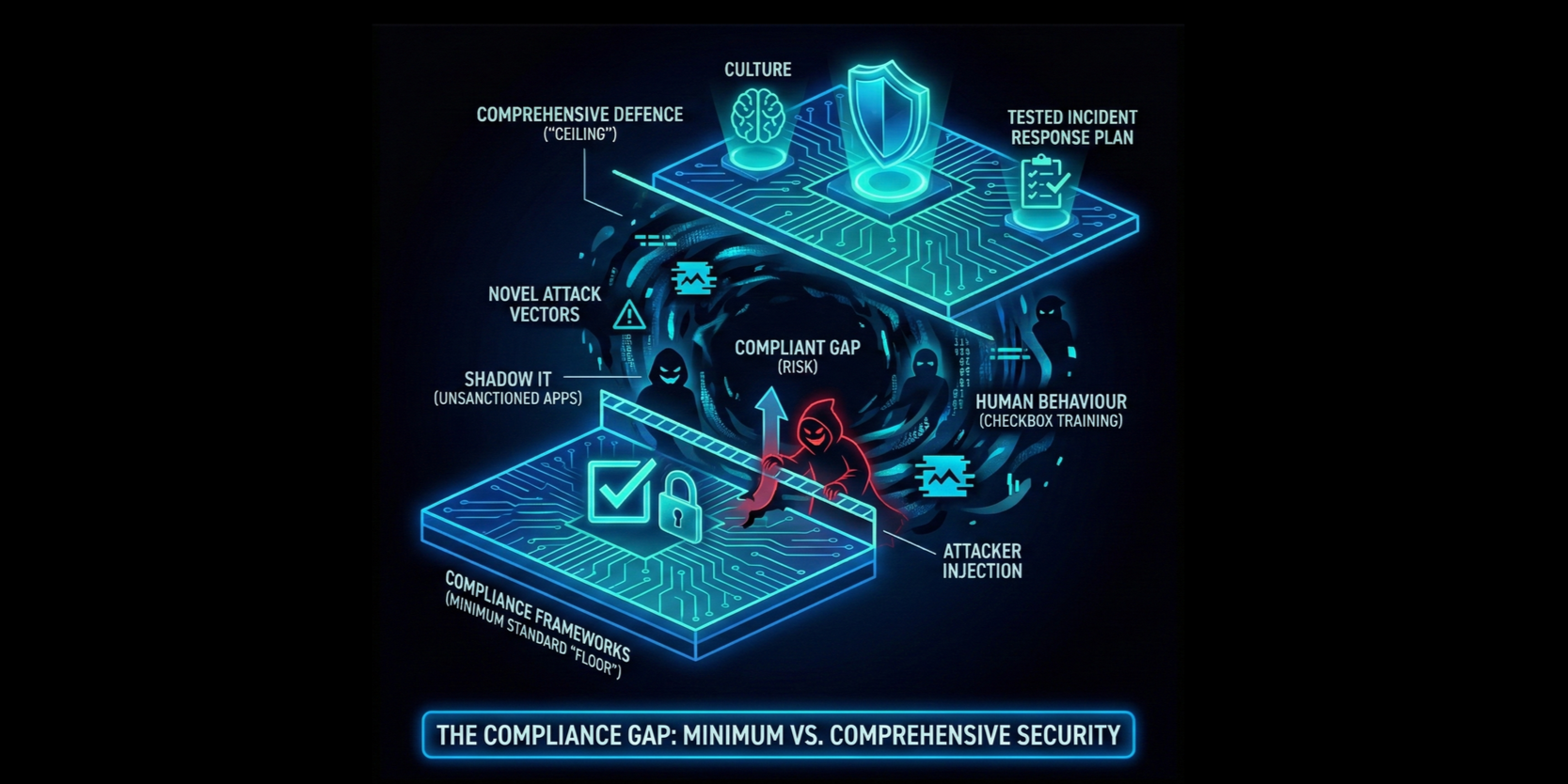
Minimum Standards vs Advanced Threats
Compliance frameworks are are designed to set a ‘floor’ for security; a minimum standard required to operate legally or contractually. Rather than a ‘ceiling’ of comprehensive defence.
Because these regulations often lag behind the pace of technological innovation, they may fail to address novel attack vectors.
This gap is evident in the distinctions between risk assessment and maturity assessments. A compliance review might verify that patches are applied, but fail to identify that the organisation hasn’t tested their new incident response plan, or doesn’t have a culture of security; leaving them vulnerable when a breach occurs.
Compliance ratings frequently overlook the unpredictable nature of human behaviour, as well as the use of unauthorised technology:
Employees often adopt unsanctioned software (Shadow IT) and connect applications or data sources to one-another (Applcation Programming Interfaces - APIs), to increase productivity, bypassing IT protocols. These create ‘data governance black holes’ and security vulnerabilities that compliance audits may miss entirely because the auditors are unaware the asset or connection exists.
An organisation can have perfect policies on paper, yet fail to foster a culture where employees actually follow them. Compliance training is often treated as a ‘checkbox’ exercise, leading to disengagement; employees may complete the training but still engage in risky behaviours as they don’t understand the risk or see the tangible benefit.
This ‘compliant’ gap between the minimum standard required and comprehensive defence is a risk in itself, and this is where attackers can inject themselves into the organisation’s environment.
The Hidden Gap for Attackers
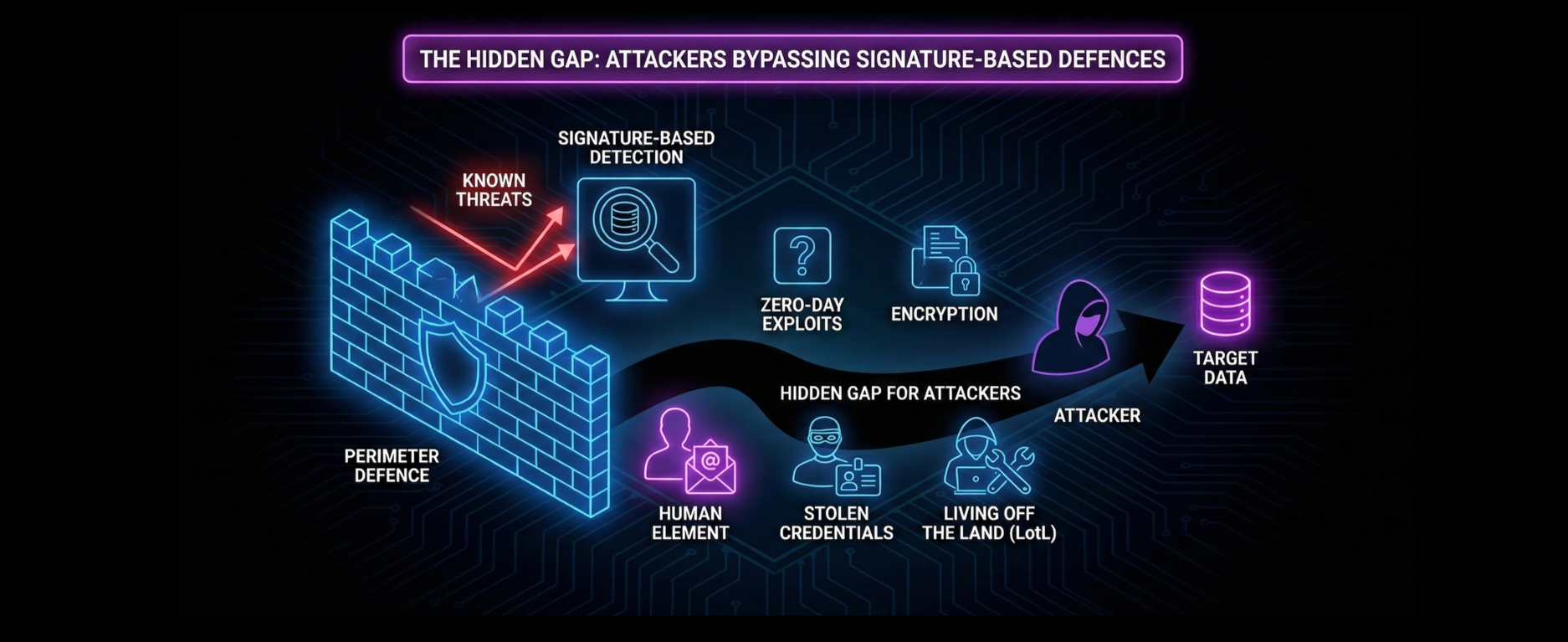
While organisations may invest heavily in technical defences, the human element often serves as the initial entry point, bypassing perimeter defences.
Signature-based detections fail to recognise the intruder once they are operating with legitimate credentials.
Signature-based detection operates on a ‘blacklist’ model, scanning for specific file hashes or code strings that match a database of known threats. This approach fails to detect malicious actions in several key scenarios:
New threats, such as zero-day exploits or new tactics haven’t been catalogued, thus won’t be detected.
Encryption used to mask attacks, rendering signature-based inspection tools useless because they can’t read the payload.
‘Legitimate User’ Blind Spot; failure of a signature detection to distinguish between a legitimate user and an attacker with stolen credentials.
An attacker Living off the Land (LotL) doesn’t flag security tools as the use of an organisation’s own legitimate software isn’t triggered as malicious.
Signature-based detection is crucial for detecting known malicious files and actions, however attackers are evolving their methods and utlising new methods that are harder to detect with commonly used detection techniques.
The Rise of the Malware-Free Attack
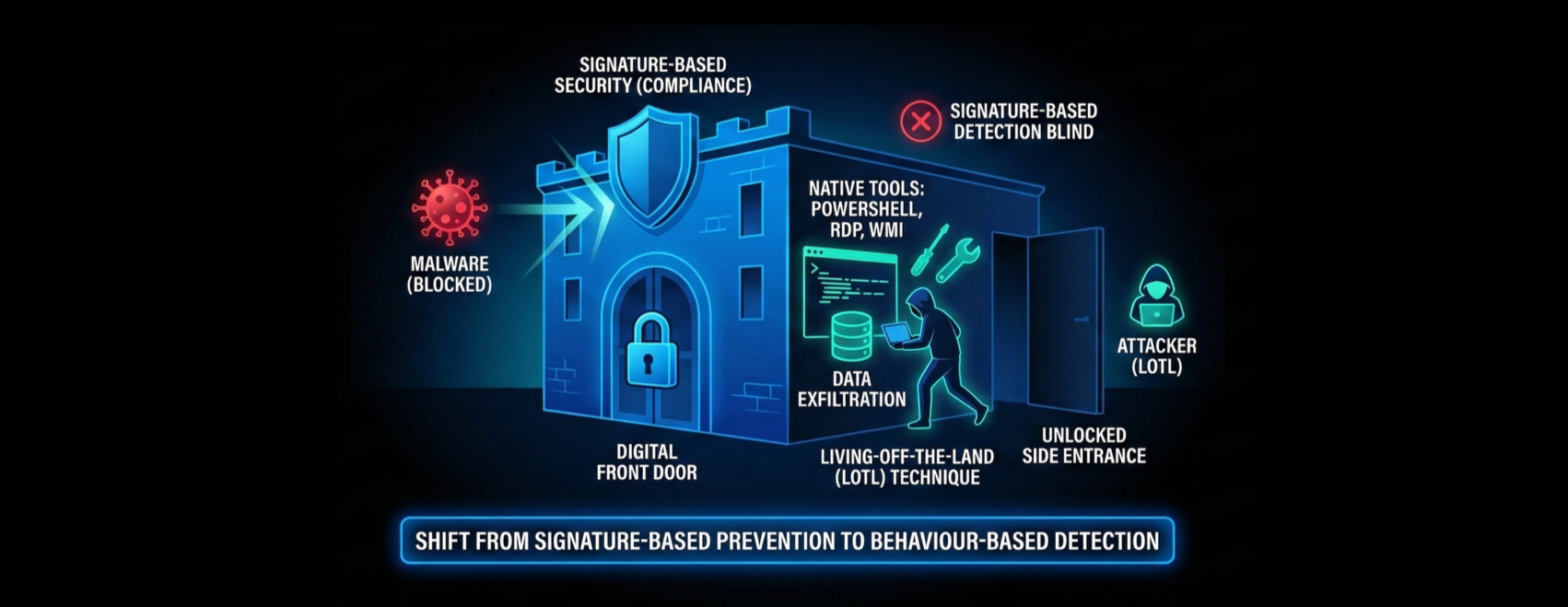
The conventional image of a cyberattack involves a virus or malware, but the reality is that the majority of modern intrusions don’t rely on malware at all. While organisations fortify their digital front door, attackers are simply walking through an unlocked side entrance.
Instead of using malware, attackers are using a technique known as “Living-off-the-Land” (LotL). Instead of introducing foreign code, they use trusted, native tools already present in the environment and essential for normal IT operations. Powerful administrative utlities like Powershell, Remote Desktop Protocol (RDP) and Windows Management Instrumentation (WMI) are repurposed to execute commands, move laterally across a network and exfiltrate data.
This is dangerously effective because it allows attackers to blend in with normal activity and bypass traditional signature-based security. Since no malware is deployed, conventional antivirus software and signature-based detections are often blind to the attack. This means that while you’re scanning for known viruses or signatures, the real threat is already inside, using your own tools to dismantle (or avoid) your defences from within.
The strategic implication is clear: security investments must pivot from purely compliance via signature-based prevention to behaviour-based detection and response.
The Superiority of Behaviour-Based Detection
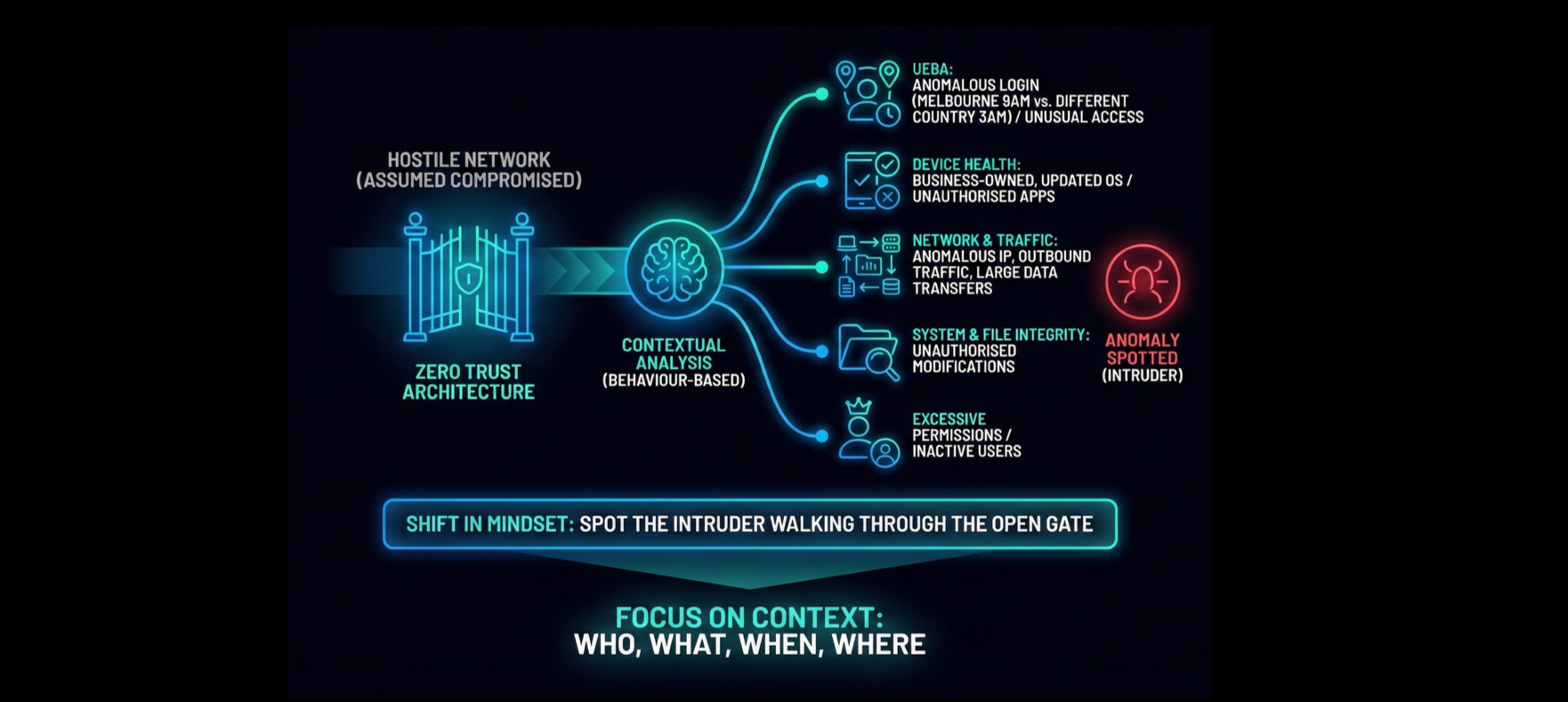
Behaviour-based detection, often implemented through Zero Trust architectures (no user or device is trusted by default), succeeds where signatures fail by assuming the network is already hostile and continuously analysing the context of activities.
Behaviour-based detection continuously monitors the actions of users, devices and applications to identify anomalies that deviate from established patterns of ‘normal’ activity, allowing it to spot threats that use legitimate credentials or novel methods:
User and Entity Behaviour Analytics (UEBA) will flag a user who usually logs in from Melbourne at 9am but attempts to log in from a different country at 3am, or a user accessing systems or data they don’t usually interact with in their daily duties.
Device health checks communicate with endpoint security software to ensure the device is business-owned and updated to the newest approved OS before and during access, as well as the presence of unauthorised or suspicious applications that could indicate a compromised device.
Network and traffic monitoring detects anomalies such as unexpected IP changes, outbound traffic, large data transfers or attempts to access critical data sources.
System and file integrity monitoring identifies unauthorised modifications to files and configurations within the environment.
Excessive permission monitoring identifies accounts with excessive permissions, or inactive users that could be exploited.
Adopting these behavioural measures requires a fundamental shift in mindset. It means accepting that the network is likely already compromised and that the goal is not just to build higher walls, but to spot the intruder walking through the open gate.
By focusing on context (who is doing what, when, and from where) organisations can detect the subtle anomalies that signal a breach long before a static compliance checklist would raise a red flag.
Conclusion: Moving Beyond the Theater
Compliance is the floor, not the ceiling. While frameworks and maturity scores provide a necessary baseline for hygiene, they remain blind to the nuances of human behaviour and sophisticated, malware-free attacks.
To survive the modern threat landscape, we must dismantle the "Security Theater." We need to shift resources away from performative box-ticking and toward dynamic, behaviour-based detection. A perfect maturity score might save your reputation in the boardroom, but only operational resilience will save your data in the real world.