The Framing Problem: Converting Subjective Cyber Risk into Objective Financial Terms
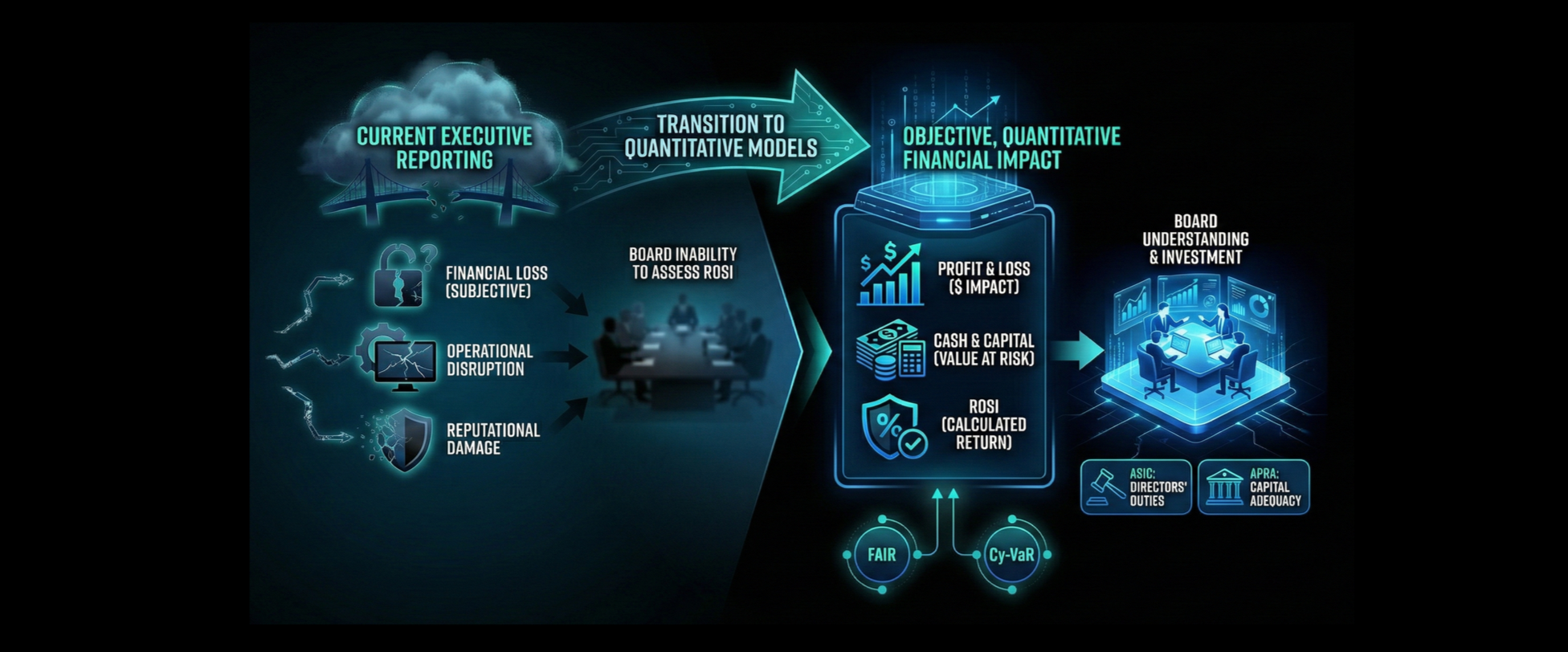
Current executive cybersecurity reporting is failing. It fails because it frames security risk using subjective, qualitative measures: "high" risk, "red" status, or abstract technical threats: (risk of) financial loss, operational disruption, reputational damage, etc.
This creates a translation error. Boards operate on the logic of finance: profit and loss, cash flow, and capital allocation. When a CISO presents a "Red Heatmap," the Board cannot intuitively calculate the Return on Security Investment (ROSI). The financial impact remains ambiguous, and consequently, capital is misallocated.
This disconnect is not just a communication issue; it is a governance risk.
ASIC enforces strict directors' duties; failure to manage cyber risk effectively can breach license obligations.
APRA mandates capital adequacy standards, requiring information security capability to be commensurate with threats.
If a Board cannot quantify the risk, they cannot effectively satisfy these requirements.
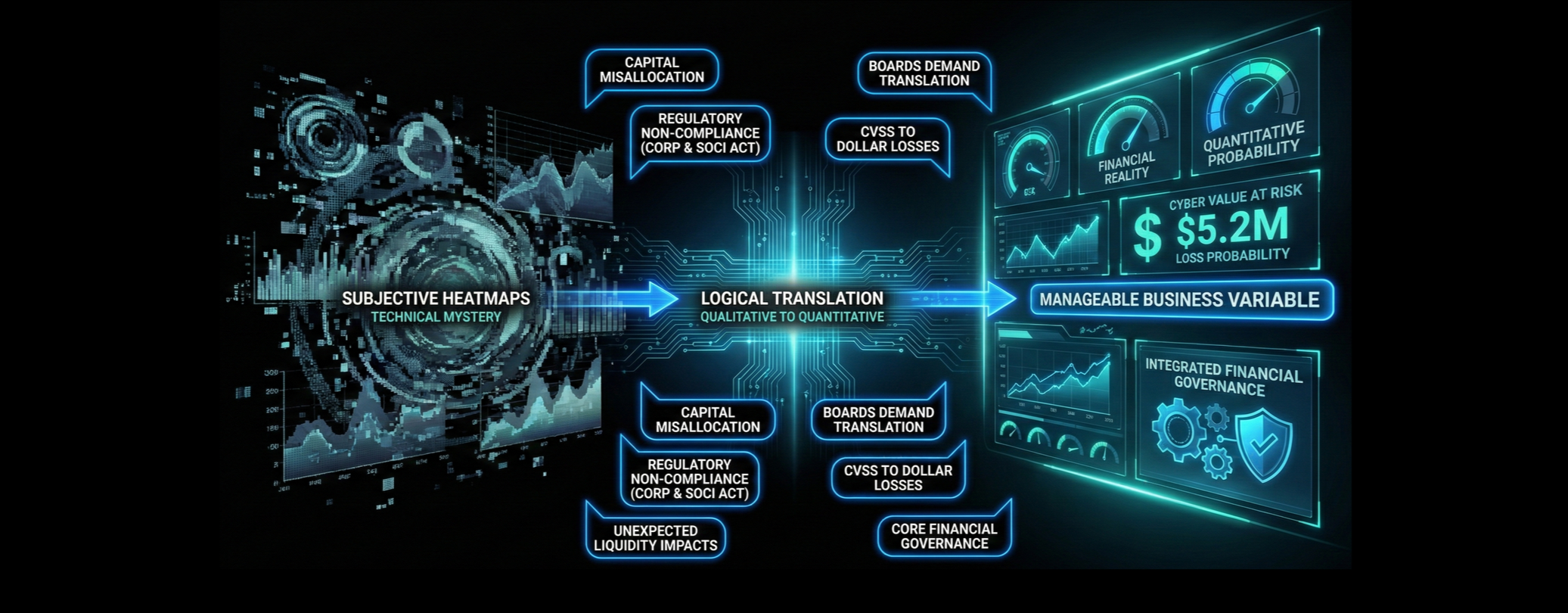
Organisations must transition from subjective heatmaps to quantitative risk models. We need to translate technical vulnerabilities into the only language that matters in the boardroom: Dollars.
To do this, we utilise models such as Factor Analysis of Information Risk (FAIR) and Cyber Value at Risk (Cy-VaR).
The FAIR model replaces "gut feeling" with a structured analysis of probability and loss magnitude. Cy-VaR calculates the maximum potential loss over a specific time frame.
By adopting this structure, cybersecurity transitions from a technical mystery to a manageable business variable.
Why Heatmaps Hide Reality
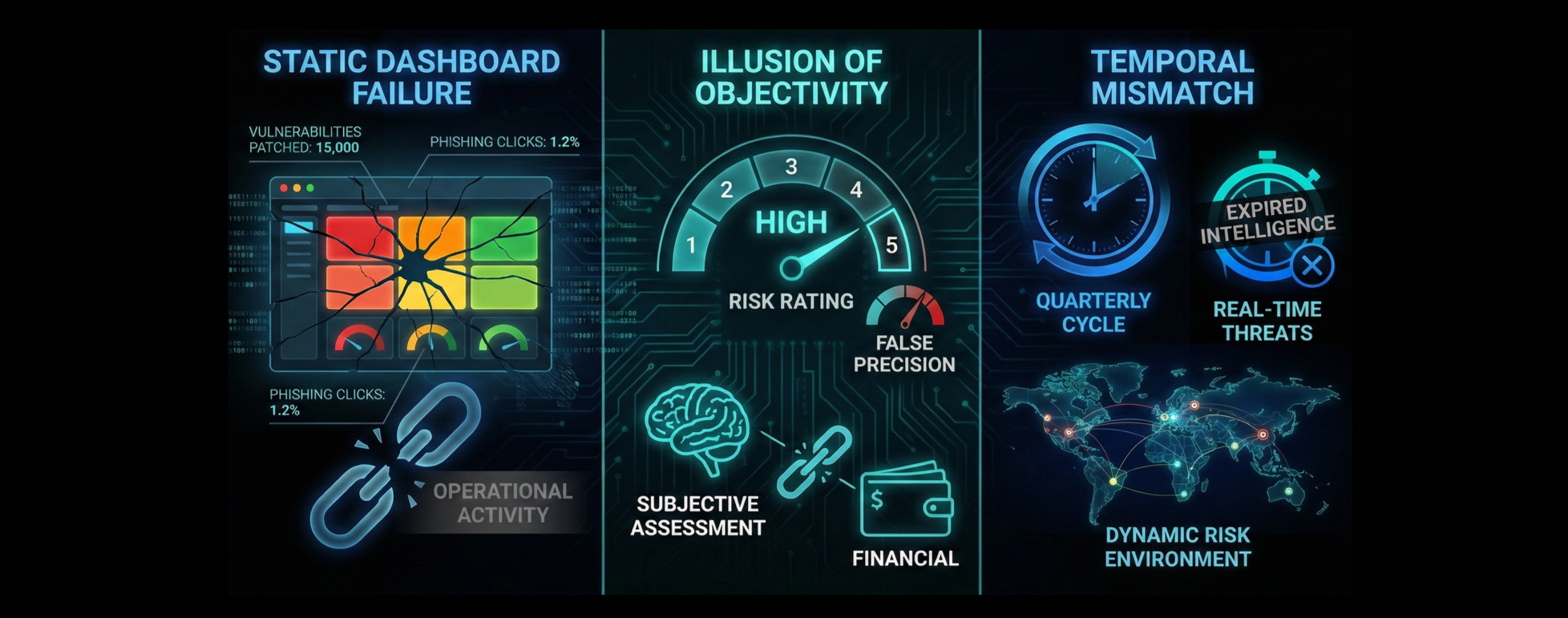
There is a fundamental disconnection between data presented in executive cybersecurity reporting and the decision-making requirements of the Board. This disconnection stems from the reliance on Red, Amber, Green (RAG) heatmaps to communicate complex risk postures.
These dashboards usually aggregate technical metrics: number of vulnerabilities patched, volume of malicious actions blocked, click rate on phishing simulations, etc.
While these metrics demonstrate operational activity, they fail to demonstrate risk reduction in economic terms.
The Illusion of Objectivity in Heatmaps
Heatmaps present an illusion of objectivity that misleads the Board. A “High” risk rating on a heat map implies a specific threshold or calculated probability, yet the categorisation often solely relies on the subjective assessment of the assessor. This approach can create a false sense of security and precision.
A risk rated 4 on a 1-5 scale suggests that it’s twice as severe as a risk rated 2, yet without financial quantification, this mathematical relationship is non-existent.
Boards and Audit Committees face a flood of poorly categorised risk reports containing inconsistent levels of detail. This lack of clarity forces executives to either ask for further information, or accept the finding as they initially “understand” it.
When a board member observes a “Red” indicator turn “Green” after allocating capital, they logically assume the risk is eliminated. In reality, the technical vulnerability may be patched, but the systemic business process risk remains if the human attack surface or third-party dependency persists. The dashboard signals safety, while the financial risk remains elevated.
The Timing Mismatch
Cyber risk is dynamic, it changes by the minute as new vulnerabilities (CVEs) emerge, threat actor tactics evolve, organisational technical landscape evolves, etc.
Traditional Enterprise Risk Management (ERM) frameworks assess risk on quarterly or annual cycles.
This mismatch renders quarterly executive cybersecurity reporting obsolete before the meeting commences. A static heatmap presented in a boardroom cannot reflect a misconfiguration that occurred three hours prior, which attackers exploit in real-time.
The industry creates snapshots of a dynamic environment and attempts to explain the narrative, resulting in a governance failure where the Board approves strategy based on expired intelligence.
The Language Barrier and Conversion
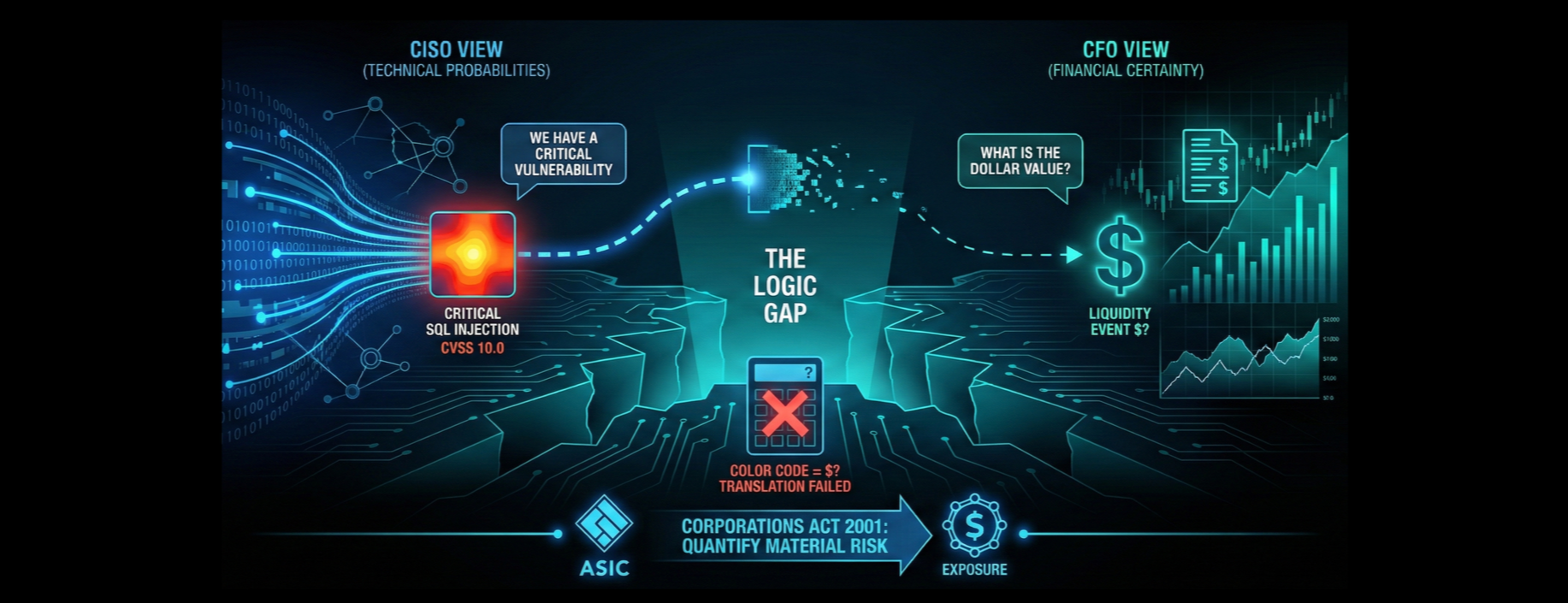
There is a critical misalignment between Information Security and the Board. It is not just a language barrier; it is a failure to convert technical probabilities into the financial certainty required for strategic decision-making.
The Subjective vs. Objective Divide
Current reporting fails to bridge the gap between technical metrics and business requirements:
Security relies on expert judgment (qualitative) to gauge severity, while Finance relies on hard data (quantitative) to calculate insurance and capital reserves.
CISO View: "We have a critical SQL injection vulnerability."
CFO View: "What is the probability of a liquidity event, and what is the dollar value?"
You cannot input a color code into a balance sheet. A CFO cannot hedge against "Red"; they can only hedge against a quantified financial exposure (e.g., "$20 million").
The Materiality Definition Conflict
Regulators now demand the translation of logic that the industry has historically ignored. Under the Corporations Act 2001 (Cth), directors must exercise care and diligence, which extends to cyber resilience.
Technologists define materiality by data volume (e.g., 10,000 records lost) or technical severity (CVSS 10.0). Regulators and investors define materiality by investment impact and market price sensitivity.
A CISO may view a DDoS attack as an operational nuisance, while the CFO views the resulting outage as a material event due to revenue recognition delays and reputational damage affecting stock volatility. Without a unified quantitative framework, the organisation faces enforcement action from ASIC for failing to disclose material business risks.
Converting Vulnerability to Liability
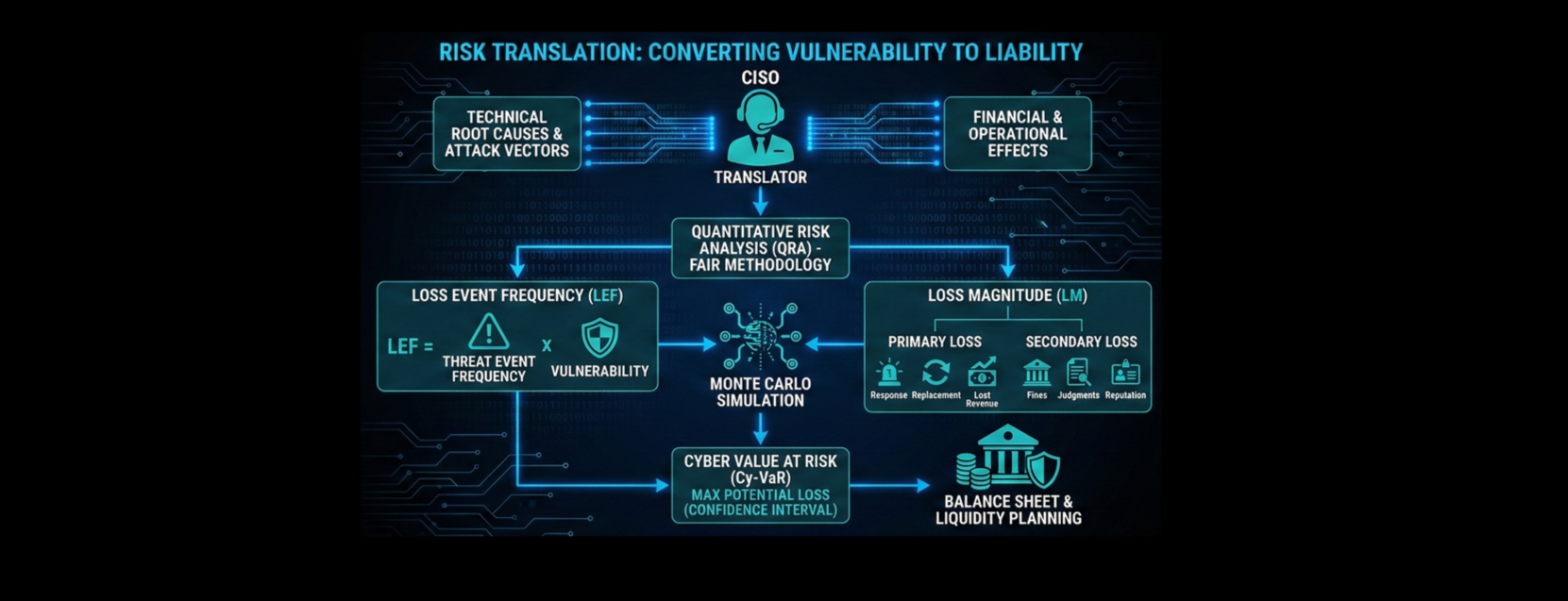
To close the logic gap, the CISO must function as a translator, converting technical root causes into financial and operational effects. This requires specific methodologies to calculate value at risk, linking specific attack vectors to specific lines on the balance sheet.
The Mathematics of Risk Quantification
To move from heatmaps to financial dashboards, organisations should adopt Quantitative Risk Analysis (QRA). The standard methodology is FAIR (Factor Analysis of Information Risk), which breaks down risk into probabilistic factors, allowing for the calculation of Annualised Loss Expectancy (ALE) and Cyber Value at Risk (Cy-VaR).
Factor Analysis of Information Risk (FAIR)
FAIR defines risk as the probable frequency and probable magnitude of future loss. It replaces typical scales (1-5) with distributions, acknowledging uncertainty.
Loss Event Frequency (LEF): How often will the bad thing happen?
Equation: LEF = Threat Event Frequency (Attempts) x Vulnerability (Probability of Success).
Note: In quantitative risk, "Vulnerability" is not just a software bug; it is the probability (percentage) that the attacker's capability exceeds the organisation's resistance strength.Example: 1000 (phishing emails) x 5% (click rate) = 50 Loss Events per year.
Loss Magnitude (LM): How much will it cost when it happens?
Primary Loss: Direct costs incurred by the organisation (incident response retainers to contain 50 compromises, reimaging laptops). Example estimate $10k - $50k per event.
Secondary Loss: Costs incurred as a result of secondary reactions (fines, judgments, reputational damage). Example estimate $2m - $10m per material breach.
FAIR inputs these variables into a Monte Carlo simulation, running the scenario 10,000+ times to produce a probability distribution curve; maps the full range of financial outcomes, distinguishing between the probable "peak" of minor operational costs and the rare "tail" scenarios that threaten solvency.
Cy-VaR focused strictly on that “tail”.
Example Monte Carlo Simulation Output
Running the Monte Carlo simulation 10,000 times for our example phishing scenario yields the following financial distribution:
Most Likely Outcome ($50,000): The "Normal" year. Routine costs for re-imaging laptops after minor compromises.
90th Percentile ($2.5 Million): A "Bad" year. A minor data leak triggering fines and notification costs.
95th Percentile ($15 Million): The "Catastrophe" (Cy-VaR). A ransomware event causes weeks of downtime and class-action lawsuits.
The organisation budgets $50,000 in operational expenditure to manage the daily risk, but holds $15 million in capital reserves (or insurance) to survive the tail risk.
Cyber Value at Risk (Cy-VaR)
While FAIR provides the engine, Cy-VaR provides the board metric. Borrowed from financial market risk management, Cy-VaR calculates the maximum potential loss over a specific time frame with a given confidence interval.
Cy-VaR = Maximum Loss ($) at (% Confidence Level) over (Time Frame).
"We have a 95% confidence that cyber losses will not exceed $15 million in the next financial year."
Banks use Cy-VaR to stress test their liquidity buffers. If a cyber event locks up 30% of liquidity, the bank must hold sufficient High-Quality Liquid Assets (HQLA) to survive the duration of the event.
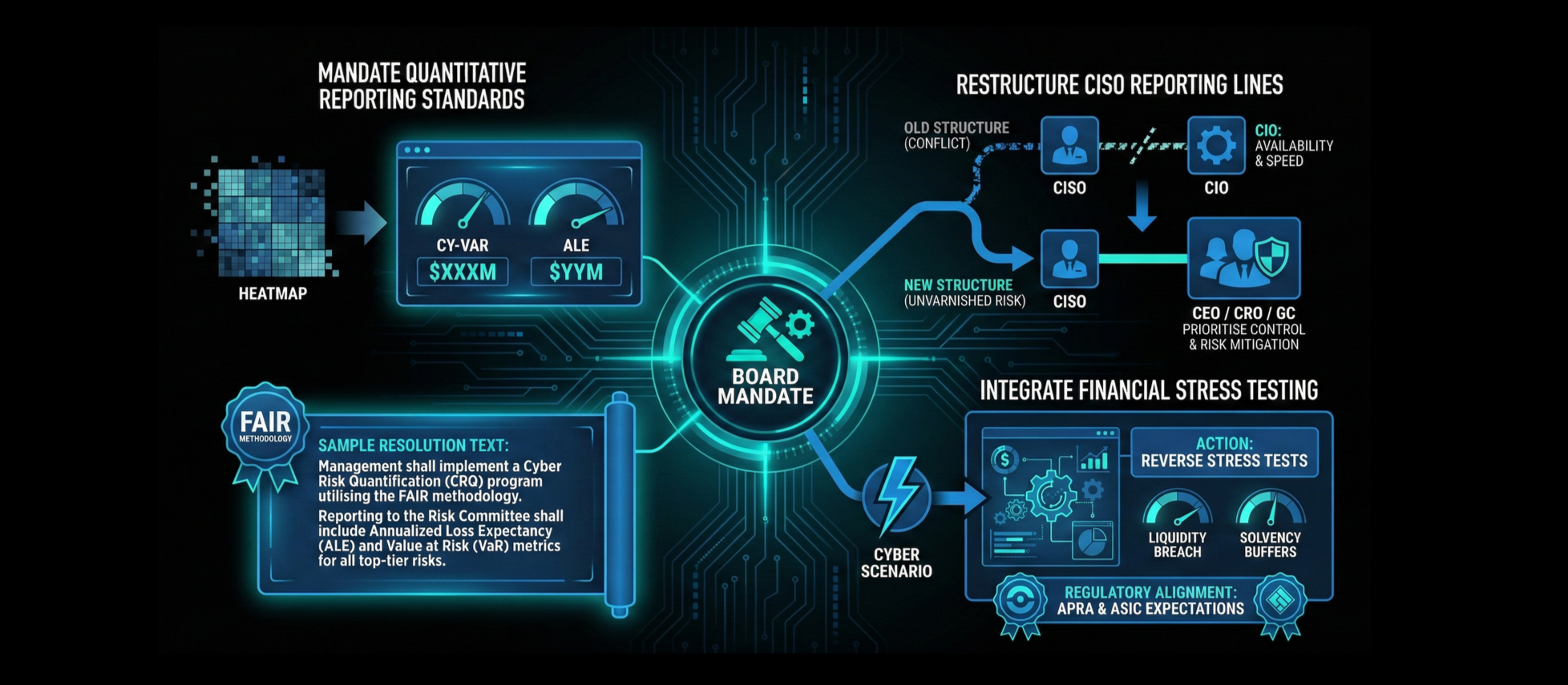
The Board Mandate
Logic dictates that if the reporting mechanism is flawed, the governance structure is flawed. Boards need to mandate a shift in how cyber risk is managed and reported to ensure fiduciary duty is met.
Mandate Quantitative Reporting Standards
The Board is obligated to pass a resolution requiring management to identify and quantify financial exposure to cyber risks.
Reports should present “Cyber Value at Risk” (Cy-VaR) and "Annualised Loss Expectancy" (ALE) rather than heatmaps.
Management should implement a Cyber Risk Quantification (CRQ) program utilising the FAIR methodology. Reporting to the Risk Committee should include Annualized Loss Expectancy (ALE) and Value at Risk (VaR) metrics for all top-tier risks.
Restructure CISO Reporting Lines
The CISO reporting to the CIO creates a structural conflict of interest. The CIO prioritises system availability and speed; the CISO prioritises control and risk mitigation.
The CISO should report to the CEO, CRO (Chief Risk Officer) or General Counsel to ensure unvarnished communication of risk.
Integrate Financial Stress Testing
Cyber scenarios should be integrated into the organisation's financial stress tests.
The Audit Committee should require "Reverse Stress Tests": identifying the scale of cyber event required to breach liquidity coverage ratios or bank solvency buffers.
This satisfies APRA's requirement for systematic testing of controls and ASIC's expectation of cyber resilience.
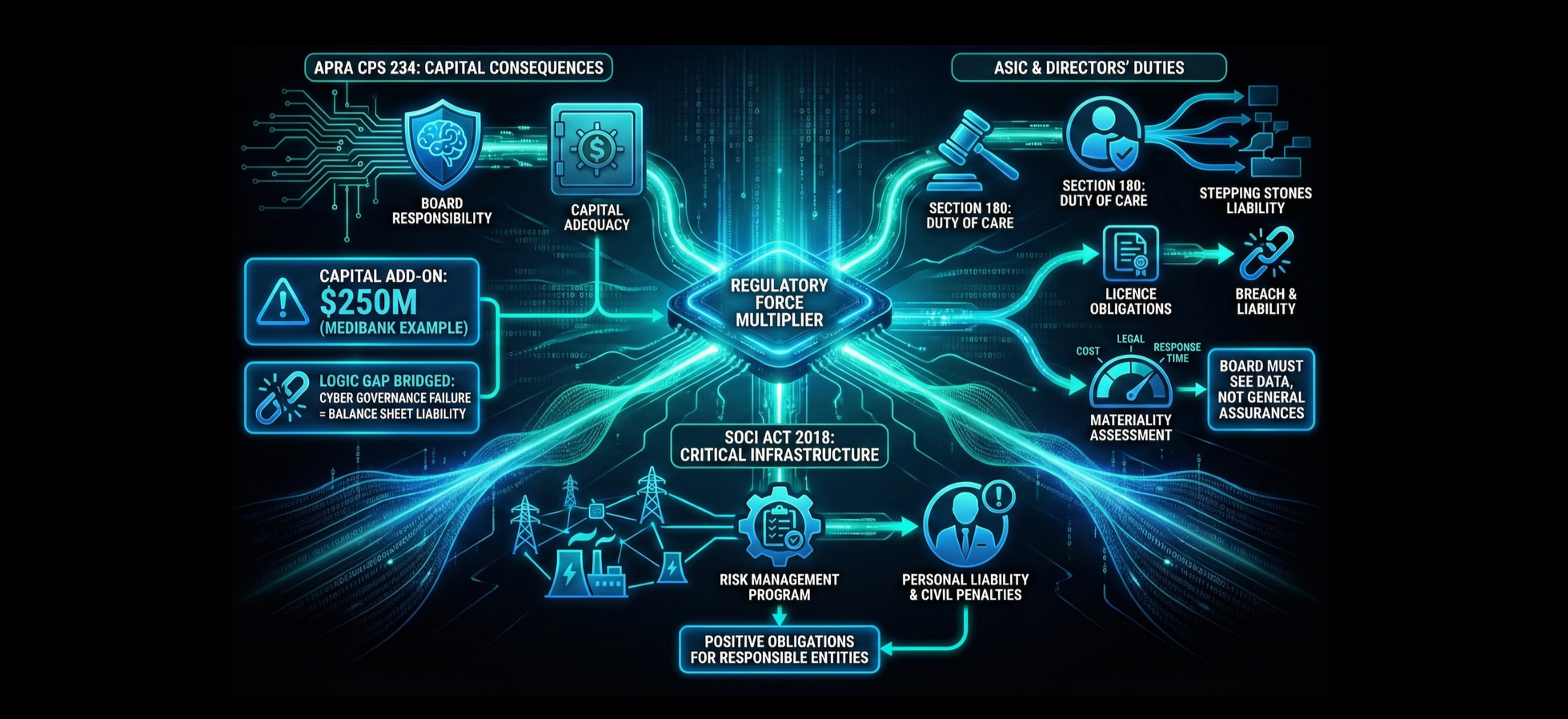
The Regulatory Force Multiplier: APRA, ASIC & SOCI
In Australia, the transition to financial risk quantification is driven by a regulatory triad: The Security of Critical Infrastructure Act 2018 (SOCI), APRA's Prudential Standard CPS 234, and ASIC's enforcement of directors' duties.
APRA CPS 234: Capital Consequences
APRA Prudential Standard CPS 234 Information Security mandates that the Board is ultimately responsible for the information security of the entity.
Boards can no longer claim ignorance of technical details. They must ensure information security capability is commensurate with threats.
APRA has demonstrated it will use capital adequacy requirements as an enforcement tool. The $250 million capital add-on applied to Medibank explicitly penalised "weaknesses identified in Medibank's information security environment". This translates cyber governance failure directly into a balance sheet liability.
ASIC and Directors' Duties
ASIC views cyber resilience as a core component of a director's duty of care and diligence under Section 180 of the Corporations Act.
A failure to manage cyber risk can lead to a breach of the company's licence obligations, which in turn triggers a breach of directors' duties.
For listed entities, "material" cyber risks must be disclosed to the market. This requires the Board to have quantitative data on potential financial impacts (lost revenue, fines, recovery costs) to accurately inform investors. General assurances are insufficient; the Board must see the data.
Security of Critical Infrastructure (SOCI) Act
The SOCI Act places positive obligations on responsible entities for critical infrastructure assets.
Entities must adopt and maintain a Critical Infrastructure Risk Management Program (CIRMP).
The Board must submit an Annual Report to the government, attesting that the risk management program is effective. Signing this attestation without quantitative evidence of risk reduction exposes Directors to significant legal and reputational risk if a breach subsequently reveals the program was inadequate.
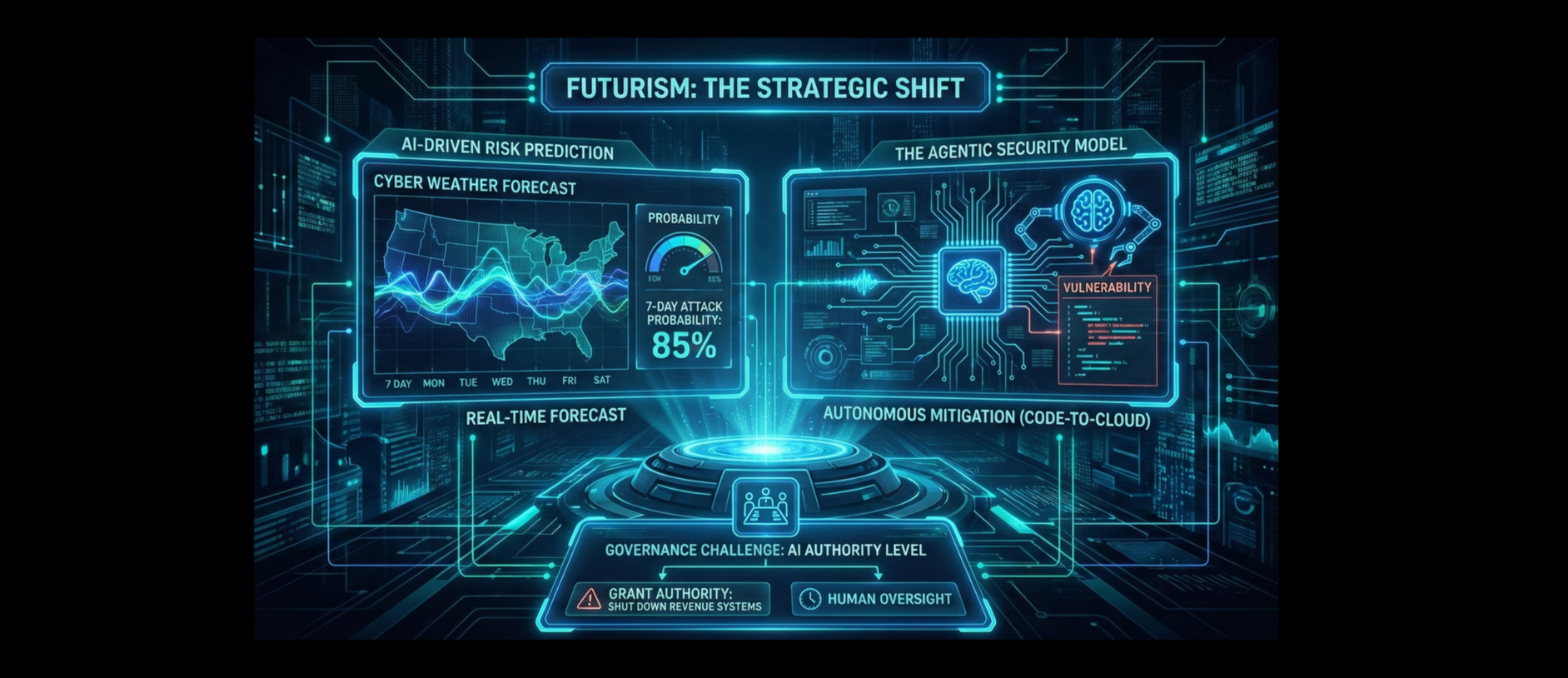
The Strategic Shift
Static dashboards are being phased out. Current threat velocities now exceed human processing speeds, making reliance on manual interpretation a critical security bottleneck.
AI-Driven Risk Prediction
Next-generation platforms utilise AI to predict exposure before it is exploited.
Deep Learning models trained on petabytes of network data identify subtle anomalies in behaviour that precede an attack.
Reporting should shift from "Quarterly Retrospective" to "Real-Time Forecast." Boards will view "Cyber Weather Forecasts"; probability of attack in the next 7 days: allowing for agile resource allocation.
These models update the risk quantification in real-time. If the AI detects a spike in threat activity, the Cyber Value at Risk (Cy-VaR) metric immediately adjusts (e.g., from $5M to $12M), ensuring the Board sees the financial reality of the threat, not just the technical probability.
The Agentic Security Model
Future systems will not just report risk; they will autonomously mitigate it. "Agentic" platforms span development to operational runtime and security operations, fixing vulnerabilities faster than human teams can approve tickets.
Boards will need to govern the AI's decision-making parameters. The risk discussion will shift to "What authority do we grant the AI to shut down revenue-generating systems to prevent a breach?"
This moves governance from approval (Human-in-the-loop) to oversight (Human-on-the-loop), requiring Boards to pre-approve the specific financial thresholds at which the AI is permitted to autonomously disrupt business operations to save the asset.
Conclusion: From Heatmaps to Financial Reality
The framing problem in cybersecurity is a failure of translation. By adhering to subjective, technical heatmaps, Australian executives remain blind to the financial reality of their risk exposure. The logic gap leads to capital misallocation, regulatory exposure under the Corporations Act and SOCI Act, and unexpected impacts on liquidity.
The solution is logical: replace qualitative judgment with quantitative probability. Boards should demand the translation of technical severity into Dollar Losses, mandate the calculation of Cyber Value at Risk (Cy-VAR), and integrate cyber resilience into the core financial governance of the institution. Only then does cybersecurity transition from a technical mystery to a manageable business variable.